Overview
According to NIST, Zero Trust (ZT) is the term for an evolving set of cybersecurity paradigms that move defences from static, network-based perimeters to focus on users, assets, and resources. A zero trust architecture (ZTA) uses zero trust principles to plan industrial and enterprise infrastructure and workflows. Zero trust assumes there is no implicit trust granted to assets or user accounts based solely on their physical or network location (i.e., local area networks versus the internet) or based on asset ownership (enterprise or personally owned).
We enable your Zero Trust approach with a wide range of solutions and practices to maximise security while minimising friction through perimeter-less control, contextual awareness, and privileged access.
Zero Trust Benefits
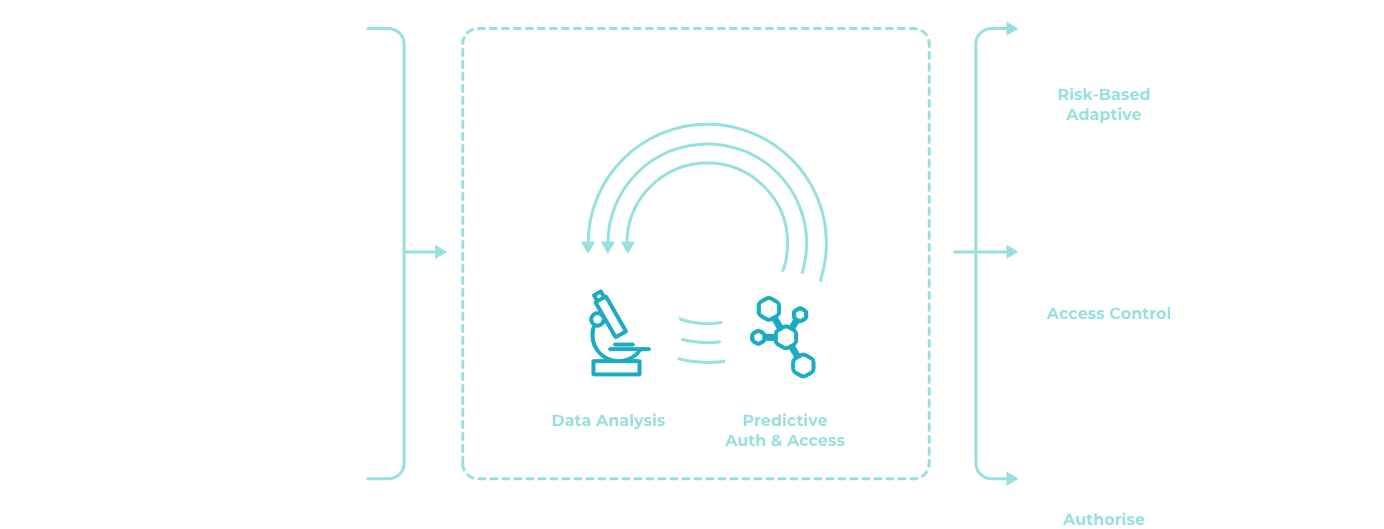
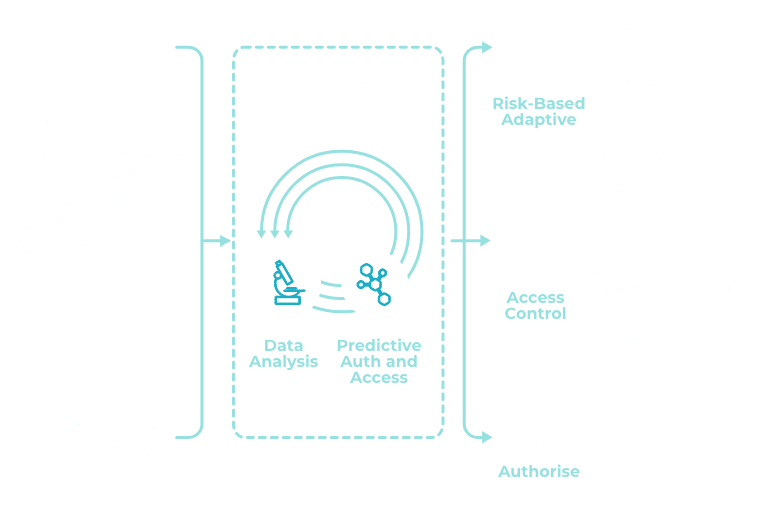
The SSS Zero Trust approach is designed for distributed teams, systems and applications. We enable your zero trust framework with solutions like least privileged access, policy enforcement and strong encryption to ensure you maintain control and visibility over your users and their devices.
- Maximum Security, Minimum Friction: Keep workforce friction to a minimum with intelligent authentication like biometrics and mobile PKI.
- Least Privileged Access: Create a context that makes sense for every user and device, with rights and access that align with the data and resources they truly need.
- Contextual Awareness: Apply device reputation and adaptive risk-based policies with step-up authentication.
- Perimeter-Free: Shift access control to individual devices and users and apply findings from behavioral data to improve security and user experience.
Our zero trust philosophy is based on our extensive knowledge of continuous authentication and the belief that seamless, secure experiences are achieved through the continual monitoring of user and device behaviour.